



Date:05/04/18
 The number of records breached dropped nearly 25% in 2017 as cyber criminals shifted focus to launching ransomware attacks, a study has revealed.
The number of records breached dropped nearly 25% in 2017 as cyber criminals shifted focus to launching ransomware attacks, a study has revealed.
Although more than 2.9 billion records were compromised, this figure is down 1.1 billion compared with 2016, with ransomware the dominant attack type, including pseudo-ransomware that is essentially designed to be destructive, according to the 2018 IBM X-Force Threat intelligence index report.
Ransomware is aimed at raising money, but does not typically involve the compromise of any data, which is simply encrypted, with payment demanded in return for the decryption key.
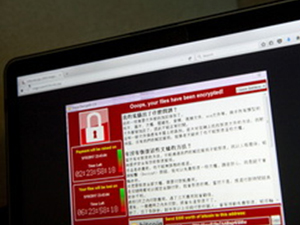
Pseudo-ransomware, however, typically locks up or wipes data and does not include any effective mechanism for collecting ransoms or delivering decryption keys, such as WannaCry and NotPetya.
The report, which is based on the analysis of data from hundreds of millions of protected endpoints and servers across nearly 100 countries, also reveals that there was a 424% increase in breaches related to misconfigured cloud infrastructure, largely due to human error.
The report shows that inadvertent errors such as misconfigured cloud infrastructure were responsible for the exposure of nearly 70% of compromised records, which indicates a growing awareness among cyber criminals of the existence of misconfigured cloud servers.
Beyond misconfigured cloud servers, individuals lured through phishing attacks represented one-third of inadvertent activity that led to a security event in 2017, which includes users clicking on a link or opening an attachment laced with malicious code, usually shared through a spam campaign launched by cyber criminals.
“Inadvertent insiders were found to be a major issue for security teams to reckon with, stressing that enterprises’ cyber security awareness programs need to keep pace with the changing landscape and provide continued role-based training for all employees,” the report said.
The financial services industry topped the list of industries with the most successful cyber attacks against it, accounting for 27% of attacks requiring investigation across all industries.
The most attacked industry sector in 2017 was the information and communications technology sector, which accounted for 33% of all attacks, followed by manufacturing (18%) and the financial sector in third place accounting for 17% of all attacks.
The report said although financial services organisations have invested heavily in cyber security technologies, cyber criminal success rate is higher due to the use of banking Trojans specifically targeting consumers and users across the industry.
For example, the report said the Gozi banking Trojan and its variants was the most-used malware against the financial services industry in 2017, noting that the malware specifically targets customers as it takes over initial banking log-in screens with prompts for consumers to enter other personal information that is then shared directly with the attacker.
The use of Gozi, considered to be run by a skilled cyber crime operation, highlights how organised crime is overtaking all other classes of actors in the financial malware-facilitated fraud scene, the report said.
“While breached records are a good indication of cyber criminal activity, it doesn’t tell the full story of 2017,” said Caleb Barlow, vice-president of threat intelligence at IBM Security.
“Last year, there was a clear focus by criminals to lock data, not just steal it, through ransomware attacks. These attacks are not quantified by records breached, but have proven to be just as – if not more – costly to organisations than a traditional data breach,” said Barlow.
“The ability to anticipate these attacks and be prepared will be critical as cyber criminals will continue to evolve their tactics to what proves most lucrative.”
The report highlights that ransomware attacks put increased pressure on targeted organisations’ incident response capability by locking up core IT infrastructure.
In addition, an IBM security study in 2017 found that a slow response can affect the cost of an attack, with incidents that took longer than 30 days to contain costing up to $1m more.
“As we move into 2018, incident response is where the growth of security investment could make a difference, along with the looming potential for combating not only ransomware threats, but also the complete spectrum of cyber threats,” the report concludes.
Ransomware puts pressure on incident response
 The number of records breached dropped nearly 25% in 2017 as cyber criminals shifted focus to launching ransomware attacks, a study has revealed.
The number of records breached dropped nearly 25% in 2017 as cyber criminals shifted focus to launching ransomware attacks, a study has revealed.Although more than 2.9 billion records were compromised, this figure is down 1.1 billion compared with 2016, with ransomware the dominant attack type, including pseudo-ransomware that is essentially designed to be destructive, according to the 2018 IBM X-Force Threat intelligence index report.
Ransomware is aimed at raising money, but does not typically involve the compromise of any data, which is simply encrypted, with payment demanded in return for the decryption key.
Pseudo-ransomware, however, typically locks up or wipes data and does not include any effective mechanism for collecting ransoms or delivering decryption keys, such as WannaCry and NotPetya.
The report, which is based on the analysis of data from hundreds of millions of protected endpoints and servers across nearly 100 countries, also reveals that there was a 424% increase in breaches related to misconfigured cloud infrastructure, largely due to human error.
The report shows that inadvertent errors such as misconfigured cloud infrastructure were responsible for the exposure of nearly 70% of compromised records, which indicates a growing awareness among cyber criminals of the existence of misconfigured cloud servers.
Beyond misconfigured cloud servers, individuals lured through phishing attacks represented one-third of inadvertent activity that led to a security event in 2017, which includes users clicking on a link or opening an attachment laced with malicious code, usually shared through a spam campaign launched by cyber criminals.
“Inadvertent insiders were found to be a major issue for security teams to reckon with, stressing that enterprises’ cyber security awareness programs need to keep pace with the changing landscape and provide continued role-based training for all employees,” the report said.
The financial services industry topped the list of industries with the most successful cyber attacks against it, accounting for 27% of attacks requiring investigation across all industries.
The most attacked industry sector in 2017 was the information and communications technology sector, which accounted for 33% of all attacks, followed by manufacturing (18%) and the financial sector in third place accounting for 17% of all attacks.
The report said although financial services organisations have invested heavily in cyber security technologies, cyber criminal success rate is higher due to the use of banking Trojans specifically targeting consumers and users across the industry.
For example, the report said the Gozi banking Trojan and its variants was the most-used malware against the financial services industry in 2017, noting that the malware specifically targets customers as it takes over initial banking log-in screens with prompts for consumers to enter other personal information that is then shared directly with the attacker.
The use of Gozi, considered to be run by a skilled cyber crime operation, highlights how organised crime is overtaking all other classes of actors in the financial malware-facilitated fraud scene, the report said.
“While breached records are a good indication of cyber criminal activity, it doesn’t tell the full story of 2017,” said Caleb Barlow, vice-president of threat intelligence at IBM Security.
“Last year, there was a clear focus by criminals to lock data, not just steal it, through ransomware attacks. These attacks are not quantified by records breached, but have proven to be just as – if not more – costly to organisations than a traditional data breach,” said Barlow.
“The ability to anticipate these attacks and be prepared will be critical as cyber criminals will continue to evolve their tactics to what proves most lucrative.”
The report highlights that ransomware attacks put increased pressure on targeted organisations’ incident response capability by locking up core IT infrastructure.
In addition, an IBM security study in 2017 found that a slow response can affect the cost of an attack, with incidents that took longer than 30 days to contain costing up to $1m more.
“As we move into 2018, incident response is where the growth of security investment could make a difference, along with the looming potential for combating not only ransomware threats, but also the complete spectrum of cyber threats,” the report concludes.
Views: 459
©ictnews.az. All rights reserved.Similar news
- Cellphone Use May Raise Cancer Risk
- Australian police pushes cyber safety education
- Vietnam aims to lead in e-government
- Senate Website Gets Hacked
- US builds net for cyber war games
- Japan enacts anti-computer virus law
- India passes law vs e-waste
- Anonymous Declares War On The City Of Orlando
- Microsoft highlights evolving dangers as online identity data proliferates
- Consumers want internet security to be provided by banks
- Government facilities targets of cyber attack
- South Korean web attacks might been war drill
- Sri Lanka to Establish National Passport Database to Increase Border Security
- Hi-tech crime agencies set to employ information security professionals
- Phone hacking and online campaign bring down the News of the World





















