



Date:28/03/16
 A new piece of malware dubbed Petya is making the rounds, and taking the threat of ransomware beyond simple file encryption activities.
A new piece of malware dubbed Petya is making the rounds, and taking the threat of ransomware beyond simple file encryption activities.
The new ransomware family appears to be the first of its kind to encrypt entire hard drives, an unusual behavior compared to that of other malware families such as Locky, CryptoWall or TeslaCrypt, which encrypt individual files. However, similar to other ransomware, the new malicious application still prompts users to pay a ransom to regain access to their files.
G DATA SecurityLabs researchers, who discovered the new threat, explain that the Petya ransomware appears to be aimed mainly at companies. They observed it being distributed via a Dropbox download link to an alleged job application portfolio, included in an email sent to human resources departments.
However, the job application portfolio downloaded via the link is instead an executable file which causes the computer to crash with a bluescreen and reboot. Upon reboot, the malware manipulates the Master Boot Record (MBR) in order to take over the reboot process.
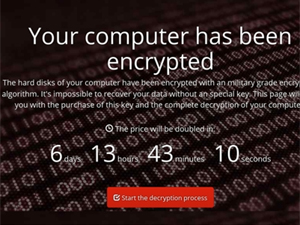
The malware then displays a message during the boot process, claiming to run a system check and to be repairing corrupted files on the system. Instead, the ransomware is locking the user out of the system and encrypting the hard drive, after which it displays a flashy warning message on the screen.
However, G DATA security researchers suggest that the user files are not encrypted at all, but that the malware only blocks file access. On the other hand, the ransom note displayed on the infected system claims that the computer has been encrypted using a “military grade encryption algorithm.”
In addition to informing users they have been compromised, the ransom note provides them with details on how they can obtain a decryption key and how they can pay for it. The malware operators are also instructing users to download and install the Tor browser and to pay the ransom using it, allowing the perpetrators to maintain their anonymity.
Petya creators provide users with a 7 days window to pay the ransom, after which they have to pay double the original amount to regain access to their files. Since this type of ransomware is new, researchers are still looking into the nefarious activity it performs on the compromised systems.
According to G DATA, HR department employees are advised to pay additional attention to the files types offered via Dropbox links, especially if they are not documents, as one would expect. The researchers also advise users to disconnect the PC from the network if they get infected, thus ensuring that other computers remain safe, and say that victims should not pay the ransom.
Petya ransomware encrypts entire hard drives
 A new piece of malware dubbed Petya is making the rounds, and taking the threat of ransomware beyond simple file encryption activities.
A new piece of malware dubbed Petya is making the rounds, and taking the threat of ransomware beyond simple file encryption activities.The new ransomware family appears to be the first of its kind to encrypt entire hard drives, an unusual behavior compared to that of other malware families such as Locky, CryptoWall or TeslaCrypt, which encrypt individual files. However, similar to other ransomware, the new malicious application still prompts users to pay a ransom to regain access to their files.
G DATA SecurityLabs researchers, who discovered the new threat, explain that the Petya ransomware appears to be aimed mainly at companies. They observed it being distributed via a Dropbox download link to an alleged job application portfolio, included in an email sent to human resources departments.
However, the job application portfolio downloaded via the link is instead an executable file which causes the computer to crash with a bluescreen and reboot. Upon reboot, the malware manipulates the Master Boot Record (MBR) in order to take over the reboot process.
The malware then displays a message during the boot process, claiming to run a system check and to be repairing corrupted files on the system. Instead, the ransomware is locking the user out of the system and encrypting the hard drive, after which it displays a flashy warning message on the screen.
However, G DATA security researchers suggest that the user files are not encrypted at all, but that the malware only blocks file access. On the other hand, the ransom note displayed on the infected system claims that the computer has been encrypted using a “military grade encryption algorithm.”
In addition to informing users they have been compromised, the ransom note provides them with details on how they can obtain a decryption key and how they can pay for it. The malware operators are also instructing users to download and install the Tor browser and to pay the ransom using it, allowing the perpetrators to maintain their anonymity.
Petya creators provide users with a 7 days window to pay the ransom, after which they have to pay double the original amount to regain access to their files. Since this type of ransomware is new, researchers are still looking into the nefarious activity it performs on the compromised systems.
According to G DATA, HR department employees are advised to pay additional attention to the files types offered via Dropbox links, especially if they are not documents, as one would expect. The researchers also advise users to disconnect the PC from the network if they get infected, thus ensuring that other computers remain safe, and say that victims should not pay the ransom.
Views: 2299
©ictnews.az. All rights reserved.Similar news
- Cellphone Use May Raise Cancer Risk
- Australian police pushes cyber safety education
- Vietnam aims to lead in e-government
- Senate Website Gets Hacked
- US builds net for cyber war games
- Japan enacts anti-computer virus law
- India passes law vs e-waste
- Anonymous Declares War On The City Of Orlando
- Microsoft highlights evolving dangers as online identity data proliferates
- Consumers want internet security to be provided by banks
- Government facilities targets of cyber attack
- South Korean web attacks might been war drill
- Sri Lanka to Establish National Passport Database to Increase Border Security
- Hi-tech crime agencies set to employ information security professionals
- Phone hacking and online campaign bring down the News of the World





















