



Date:16/05/17
 An anonymous 22-year-old security researcher who goes by MalwareTech has, at least temporarily, managed to find a kill switch for the ransomware that spread across the globe yesterday. He insists his discovery was entirely accidental but experts credit his quick action for mostly stopping the malware from spreading to the United States.
An anonymous 22-year-old security researcher who goes by MalwareTech has, at least temporarily, managed to find a kill switch for the ransomware that spread across the globe yesterday. He insists his discovery was entirely accidental but experts credit his quick action for mostly stopping the malware from spreading to the United States.
Cybersecurity professionals have been working overtime the past 24 hours as one of the largest ransomware attacks ever recorded managed to affect the systems of almost 100 countries. In the U.K., hospitals were unable to take care of patients and had to attempt to carry on operations without the use of their computer networks. Systems in Russia, Taiwan, and Spain appear to have been hit hardest. Despite some companies like FedEx reporting infection, the United States has, so far, been fairly lucky.
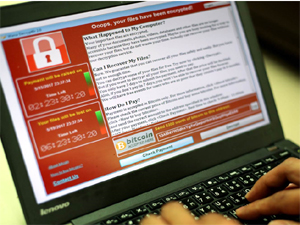
The ransomware is known as WannaCrypt and is a variant of WannaCry. It’s believed to be the first time NSA hacking tools that were leaked in April have been weaponised against the general public. MalwareTech was an essential resource for updates on the spread of the malware yesterday, and while conducting his research, he noticed that it was connecting to a domain with a long string of letters. He checked if iuqerfsodp9ifjaposdfjhgosurijfaewrwergwe- a.com was registered and found that it was available for only $10.69. It turns out that the domain was intended to be a backup plan for the malicious hackers in case they wanted to stop the spread of WannaCrypt. As soon as the domain was registered, thousands of connections a second began flooding in.
“Initially someone had reported the wrong way round that we had caused the infection by registering the domain, so I had a mini freak out until I realized it was actually the other way around and we had stopped it,” MalwareTech tells The Guardian. Matthieu Suiche, founder of cybersecurity firm Comae Technologies, credits the registration of the domain with halting the spread of the malware to systems in the United States. “The kill switch is why the U.S. hasn’t been touched so far,” he tells the New York Times. “But it’s only temporary. All the attackers would have to do is create a variant of the hack with a different domain name. I would expect them to do that.”
Indeed, the malware is expected to stick around for years. It takes advantage of an older exploit found in Windows. WannaCrypt locks up user’s systems and demands an oddly modest ransom. In order to receive the key for their encrypted files, victims are asked to pay $300 in Bitcoin. After a few days, the price rises to $600 and after seven days, the data will be locked permanently. No one is certain who is behind the attack at the moment.
In order to protect themselves, everyone should make sure that their Windows system is fully updated. Microsoft released a patch to fix this vulnerability two months ago. And even though the software giant stopped supporting Windows XP in 2014, Microsoft has released an emergency patch for that outdated operating system.
Global Ransomware Attack Accidentally Halted But Its Probably Not Over
 An anonymous 22-year-old security researcher who goes by MalwareTech has, at least temporarily, managed to find a kill switch for the ransomware that spread across the globe yesterday. He insists his discovery was entirely accidental but experts credit his quick action for mostly stopping the malware from spreading to the United States.
An anonymous 22-year-old security researcher who goes by MalwareTech has, at least temporarily, managed to find a kill switch for the ransomware that spread across the globe yesterday. He insists his discovery was entirely accidental but experts credit his quick action for mostly stopping the malware from spreading to the United States.Cybersecurity professionals have been working overtime the past 24 hours as one of the largest ransomware attacks ever recorded managed to affect the systems of almost 100 countries. In the U.K., hospitals were unable to take care of patients and had to attempt to carry on operations without the use of their computer networks. Systems in Russia, Taiwan, and Spain appear to have been hit hardest. Despite some companies like FedEx reporting infection, the United States has, so far, been fairly lucky.
The ransomware is known as WannaCrypt and is a variant of WannaCry. It’s believed to be the first time NSA hacking tools that were leaked in April have been weaponised against the general public. MalwareTech was an essential resource for updates on the spread of the malware yesterday, and while conducting his research, he noticed that it was connecting to a domain with a long string of letters. He checked if iuqerfsodp9ifjaposdfjhgosurijfaewrwergwe- a.com was registered and found that it was available for only $10.69. It turns out that the domain was intended to be a backup plan for the malicious hackers in case they wanted to stop the spread of WannaCrypt. As soon as the domain was registered, thousands of connections a second began flooding in.
“Initially someone had reported the wrong way round that we had caused the infection by registering the domain, so I had a mini freak out until I realized it was actually the other way around and we had stopped it,” MalwareTech tells The Guardian. Matthieu Suiche, founder of cybersecurity firm Comae Technologies, credits the registration of the domain with halting the spread of the malware to systems in the United States. “The kill switch is why the U.S. hasn’t been touched so far,” he tells the New York Times. “But it’s only temporary. All the attackers would have to do is create a variant of the hack with a different domain name. I would expect them to do that.”
Indeed, the malware is expected to stick around for years. It takes advantage of an older exploit found in Windows. WannaCrypt locks up user’s systems and demands an oddly modest ransom. In order to receive the key for their encrypted files, victims are asked to pay $300 in Bitcoin. After a few days, the price rises to $600 and after seven days, the data will be locked permanently. No one is certain who is behind the attack at the moment.
In order to protect themselves, everyone should make sure that their Windows system is fully updated. Microsoft released a patch to fix this vulnerability two months ago. And even though the software giant stopped supporting Windows XP in 2014, Microsoft has released an emergency patch for that outdated operating system.
Views: 437
©ictnews.az. All rights reserved.Similar news
- Cellphone Use May Raise Cancer Risk
- Australian police pushes cyber safety education
- Vietnam aims to lead in e-government
- Senate Website Gets Hacked
- US builds net for cyber war games
- Japan enacts anti-computer virus law
- India passes law vs e-waste
- Anonymous Declares War On The City Of Orlando
- Microsoft highlights evolving dangers as online identity data proliferates
- Consumers want internet security to be provided by banks
- Government facilities targets of cyber attack
- South Korean web attacks might been war drill
- Sri Lanka to Establish National Passport Database to Increase Border Security
- Hi-tech crime agencies set to employ information security professionals
- Phone hacking and online campaign bring down the News of the World





















