



Date:15/05/20
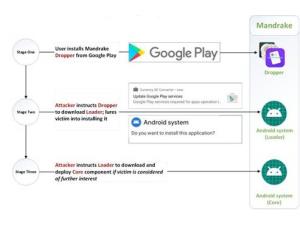 A team of security researchers at Bitdefender Labs has uncovered details of a new piece of malware infecting Android devices (via ZDNet). Referred to as Mandrake, the malware behaves somewhat differently from most common threats, as it makes an effort not to infect every device, according to Bitdefender. Instead, it cherry-picks users it can get more useful data from, since a wider spread would make it more likely to be detected.
A team of security researchers at Bitdefender Labs has uncovered details of a new piece of malware infecting Android devices (via ZDNet). Referred to as Mandrake, the malware behaves somewhat differently from most common threats, as it makes an effort not to infect every device, according to Bitdefender. Instead, it cherry-picks users it can get more useful data from, since a wider spread would make it more likely to be detected.
The malware is actually specifically instructed to not attack users in certain regions, including former Soviet Union countries, Africa, and the Middle East. Australia seems to be a highly targeted country, but America, Canada, and some European countries have also seen a high number of infections.
The malware was first detected earlier this year, but it's been around since 2016, and it's estimated that it has infected hundreds of thousands of people in that time, with tens of thousands infected in the current wave.
The reason it's able to go undetected by the Play Store is that the malware is not actually included in the apps themselves. The apps use a process that downloads the malicious payload only when directly instructed to do so, which the operators behind the malware avoid doing in Google's testing. Once the payload is on the device, the malware can obtain almost any data it wants from the user, including login credentials to websites and apps. It can actually re-draw everything that's on the screen, so what appears to be a perfectly normal app is actually granting permissions and data to the operators of the malware.
Bogdan Botezatu, director of threat research and reporting at Bitdefender, called Mandrake "one of the most potent pieces of Android malware" yet. The goal is ultimately to have complete control of the device and compromise user accounts.
In order to remain undetected, Mandrake has actually been spread using a variety of apps on the Play Store over the years, with many new ones being created, including under different developer names. The apps used to spread the malware are also relatively well supported in order to maintain the illusion that the app can be trusted - developers often respond to feedback, and many of the apps also have social media pages associated with them. Finally, once it has collected all the data it wants, the malware can completely erase itself from a device, leaving users unaware of what might have happened.
Google did not respond to ZDNet's request for comment on the matter, and it's likely that the threat is still active in one way or another. The best way to avoid this kind of malware is to ensure you install apps from reputable and trustworthy developers.
Mandrake Android malware has been stealing data since 2016
 A team of security researchers at Bitdefender Labs has uncovered details of a new piece of malware infecting Android devices (via ZDNet). Referred to as Mandrake, the malware behaves somewhat differently from most common threats, as it makes an effort not to infect every device, according to Bitdefender. Instead, it cherry-picks users it can get more useful data from, since a wider spread would make it more likely to be detected.
A team of security researchers at Bitdefender Labs has uncovered details of a new piece of malware infecting Android devices (via ZDNet). Referred to as Mandrake, the malware behaves somewhat differently from most common threats, as it makes an effort not to infect every device, according to Bitdefender. Instead, it cherry-picks users it can get more useful data from, since a wider spread would make it more likely to be detected.The malware is actually specifically instructed to not attack users in certain regions, including former Soviet Union countries, Africa, and the Middle East. Australia seems to be a highly targeted country, but America, Canada, and some European countries have also seen a high number of infections.
The malware was first detected earlier this year, but it's been around since 2016, and it's estimated that it has infected hundreds of thousands of people in that time, with tens of thousands infected in the current wave.
The reason it's able to go undetected by the Play Store is that the malware is not actually included in the apps themselves. The apps use a process that downloads the malicious payload only when directly instructed to do so, which the operators behind the malware avoid doing in Google's testing. Once the payload is on the device, the malware can obtain almost any data it wants from the user, including login credentials to websites and apps. It can actually re-draw everything that's on the screen, so what appears to be a perfectly normal app is actually granting permissions and data to the operators of the malware.
Bogdan Botezatu, director of threat research and reporting at Bitdefender, called Mandrake "one of the most potent pieces of Android malware" yet. The goal is ultimately to have complete control of the device and compromise user accounts.
In order to remain undetected, Mandrake has actually been spread using a variety of apps on the Play Store over the years, with many new ones being created, including under different developer names. The apps used to spread the malware are also relatively well supported in order to maintain the illusion that the app can be trusted - developers often respond to feedback, and many of the apps also have social media pages associated with them. Finally, once it has collected all the data it wants, the malware can completely erase itself from a device, leaving users unaware of what might have happened.
Google did not respond to ZDNet's request for comment on the matter, and it's likely that the threat is still active in one way or another. The best way to avoid this kind of malware is to ensure you install apps from reputable and trustworthy developers.
Views: 499
©ictnews.az. All rights reserved.Similar news
- Cellphone Use May Raise Cancer Risk
- Australian police pushes cyber safety education
- Vietnam aims to lead in e-government
- Senate Website Gets Hacked
- US builds net for cyber war games
- Japan enacts anti-computer virus law
- India passes law vs e-waste
- Anonymous Declares War On The City Of Orlando
- Microsoft highlights evolving dangers as online identity data proliferates
- Consumers want internet security to be provided by banks
- Government facilities targets of cyber attack
- South Korean web attacks might been war drill
- Sri Lanka to Establish National Passport Database to Increase Border Security
- Hi-tech crime agencies set to employ information security professionals
- Phone hacking and online campaign bring down the News of the World





















